wpsauron - Audit a secured wordpress website without sending requests to it
Wpsauron
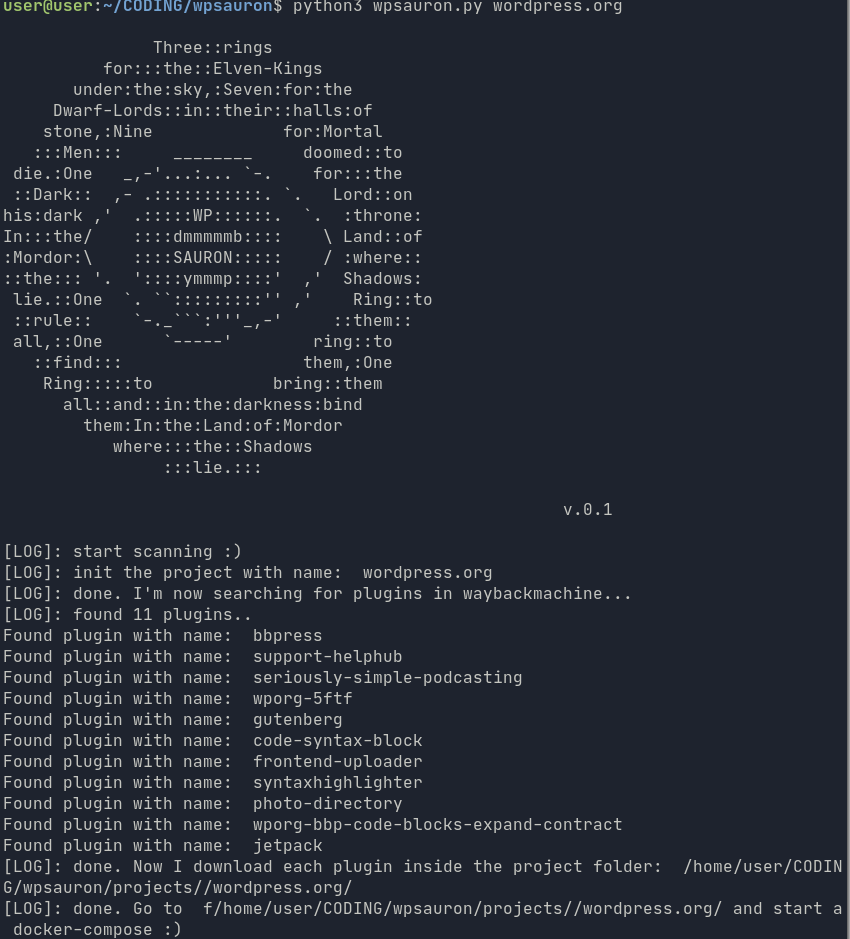
WpSauron is a simple script that helps the penetration tester aid patched wordpress websites, by creating a docker-compose environment that can be used to perform static and dynamic code analysis quickly.
With patched wordpress website I mean:
- Wordpress core is updated and no public exploit
- Plugin/themes are updates
- a WAF / some firewall solutions it is in place and you cannot send to many requests
- You tried everything else and static/dinamically code analysis is your last resort
How it works
- You give wpsauron a wordpress website url
- WpSauron fetches waybackmachines and grep plugins name
- WpSauron downloades all the found plugins
- WpSauron creates a Ready-To-Use Docker-compose
- You can now perform static-dynamic analysis against the plugins, without sending a single request
installation
-
clone the repo: github
-
create a virtual env and install requirements
python3 -m venv venv
source venv/bin/activate/
pip install -r requirements.txt
- launch the script
usage: wpsauron.py [-h] [--subdomains] domain
Passively scan a wordpress site and grabs installed plugins. Then creates a test
development for static and dynamic code analysis
positional arguments:
domain the domain name to analyze (example: test.com)
optional arguments:
-h, --help show this help message and exit
--subdomains include subdomains in the initial passive scan
- after navigate to the project dir and turn on the docker-compose
docker-compose up
remember to validate the output
How course, for each found plugin, you have to validate if it is in still use.
to be developed in the next versions
- automatically get plugin versions
- manually feed a list of plugins/versions/urls
- support active mode
- add SAST support (automatic semgrep, automatic wpbullet, automatic grep queries)